- Portals
- The Current Year
- ED in the News
- Admins
- Help ED Rebuild
- Archive
- ED Bookmarklet
- Donate Bitcoin
Contact an admin on Discord or EDF if you want an account. Also fuck bots.
Skript kiddie

U GOT HAXED



Skript Kiddies, Script Kiddies, Skids, or Script Kittens are individuals who go about trying to cause things to happen using computers that, are either frowned upon, unexpected, or malicious in nature. The tragedy of the typical script kiddie is that he approaches software the way a priest approaches the eucharist: he is so in awe at the magic of computers, that he looks to them like a sacrament from God. He therefore does not have the patience or the mental stamina to 'hack', and so uses the scripts and programs developed by others to wreak havoc on those lazy bums who cannot bother to secure their systems.
Most script kiddies spend most of their time on IRC (usually from g00ns, #calmdown on anonnet) trumpeting their 1337 h4X0ring skillz. They are usually teenagers looking for social acceptance through the internets. The majority of script kiddies are boys, but there are a few boys pretending to be girls around as well. Naturally, since most of these kids are too nerdy to get a date IRL, gaining the attention of the opposite sex is often the motive for much script kiddie exploits. Crews are formed, alliances shift, jealousies inflame -- all for a little fame that the rest of the world is oblivious towards.
To call someone a script kiddie is usually to insult their intellect, saying to the person: 'you wish to be considered a hacker, but you cannot teach yourself to develop the tools necessary to accomplish what you want'.
Script kiddies are known for blanking wiki pages and writing U GOT HAXED. They also find it very fun to exploit coding vulnerabilities.
The word skid very aptly means fart when using the unknown scripting language known as Danish.
Skript kiddie fashion and habits
Due to their usually underaged b& status, skript kiddies have an obsessive tendency towards:
- making things look obnoxious in an ADHD way, meaning blinking text, animated backgrounds, and horrible forced technomusic that has nothing to do with a keygen program.
- Using overly "cool" and "industrial" things like phosphor green, consoles, naïve admiration of cyber-punk, and Matrix-style hero complexes.
Where this differs from your twenty-something or thirty-something hacker/coder/IT-specialist is its obsessive nature and the disconnection between the pragmatic origin (eg. phosphor screens: reality on Apple II, console: faster to write a CLI than a GUI) of the phenomenon and its superficial advertisement and bricolage. Skript kiddies use these things as a status symbol, like the(now dethroned) leading fucks of Soviet Union used the hammer and sickle.
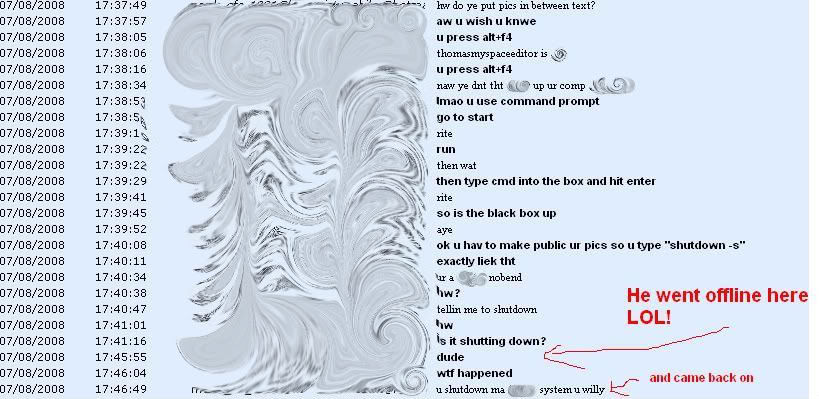
Some have to learn the hard way.
How to be a skript kiddie

- View source
- Simply become a user of chatnets or:
- Download BackTrack Linux, nmap, sshnuke, a CS wallhack tool, Back Orifice, NetBus, SubSeven, and all sorts of botnet tools.
- Gather and/or join a botnet.
- Talk out of your ass.
- Hack every IP you see.
- DDoS every IP you can't hack.
- Troll everyone you can't DDoS.
- Hack everyone you can't troll.
- Email bomb the admins you can't hack.
- Brag about stuff you didn't even do.
- Call other hackers script kiddies.
- Troll everyone who calls you a script kiddie.
- Put a floodnet on #wikipedia.
- Blank pages on every wiki you find.
- Call everything that walks a fucktard.
- Download other hackers' tools then claim that you wrote them.
- Get beaten up by your friends who you hacked by accident.
- Get banned from the internet.
- Threaten to kill yourself and blame your hacker friends when you get arrested.
- Boners.
- ????
- Profit!
Skript kiddie inventions
Most of them are batch scripts full of false command and unnecessary pauses to make it look like it actually works.
Scriptkiddie thoughts:
Hey, maybe people will think I'm a die-hard programmer if I add this!!
ECHO p.11.1..11..1.12..21.1111.000..d..5..6.6.7.7.7.7.7.77.0.0.0.0.0.0
Translation into 1337
Just so Skript Kiddies can understand, here is the entire article written in 1337.
U G0T H4X3D
Skr1pt K1dd13s, Scr1pt K1dd13s 0r s'K1dd13s 4r3 1nd1v1du4ls wh0 g0 4b0ut try1ng t0 c4us3 th1ngs t0 h4pp3n us1ng c0mput3rs th4t 4r3 31th3r fr0wn3d up0n, un3xp3ct3d 0r m4l1c10us 1n n4tur3. Th3 tr4g3dy 0f th3 typ1c4l scr1pt k1dd13 1s th4t h3 4ppr04ch3s s0ftw4r3 th3 w4y 4 pr13st 4ppr04ch3s th3 3uch4r1st: h3 1s s0 1n 4w3 4t th3 m4g1c 0f c0mput3rs, th4t h3 l00ks t0 1t l1k3 4 s4cr3m3nt fr0m G0d. H3 th3r3f0r3 d03s n0t h4v3 th3 p4t13nc3 0r th3 m3nt4l st4m1n4 t0 'h4ck', 4nd s0 us3s th3 scr1pts 4nd pr0gr4ms d3v3l0p3d by 0th3rs t0 wr34k h4v0c 0n th0s3 l4zy bums wh0 c4nn0t b0th3r t0 s3cur3 th31r syst3ms.
M0st scr1pt k1dd13s sp3nd m0st 0f th31r t1m3 0n 1RC trump3t1ng th31r 1337 h4X0r1ng sk1llz. Th3y 4r3 usu4lly t33n4g3rs l00k1ng f0r s0c14l 4cc3pt4nc3 thr0ugh th3 1nt3rn3ts. Th3 m4j0r1ty 0f scr1pt k1dd13s 4r3 b0ys, but th3r3 4r3 4 f3w b0ys pr3t3nd1ng t0 b3 g1rls 4r0und 4s w3ll. N4tur4lly, s1nc3 m0st 0f th3s3 k1ds 4r3 t00 n3rdy t0 g3t 4 d4t3 1n r34l l1f3, g41n1ng th3 4tt3nt10n 0f th3 0pp0s1t3 s3x 1s 0ft3n th3 m0t1v3 f0r much scr1pt k1dd13 3xpl01ts. Cr3ws 4r3 f0rm3d, 4ll14nc3s sh1ft, j34l0us13s 1nfl4m3 -- 4ll f0r 4 l1ttl3 f4m3 th4t th3 r3st 0f th3 w0rld 1s 0bl1v10us t0w4rds.
T0 c4ll s0m30n3 4 scr1pt k1dd13 1s usu4lly t0 1nsult th31r 1nt3ll1g3nc3, s4y1ng t0 th3 p3rs0n: 'y0u w1sh t0 b3 c0ns1d3r3d 4 h4ck3r, but y0u c4nn0t t34ch y0urs3lf t0 d3v3l0p th3 t00ls n3c3ss4ry t0 4cc0mpl1sh wh4t y0u w4nt'.
Scr1pt k1dd13s 4r3 kn0wn f0r bl4nk1ng w1k1 p4g3s 4nd wr1t1ng U G0T H4X3D.
5kr1pt k1dd13z |3e 1i|<3 d|5
|)u3 70 7|-|3|r u5u411`/ u|\||)3r493|) 8& 5747u5 5|<r||>7 |<||)|)|35 |-|4\/3 4|\| 085355|\/3 73|\||)3|\|(`/ 70\\/4r|)5:
- M4|<||\|9 7|-|||\|95 100|< 08|\|0><|0u5 ||\| 4|\| 4|)|-||) \\/4`/, M34|\|||\|9 81||\||<||\|9 73><7, 4|\||M473|) 84(|<9r0u|\||)5, |-|0rr|813 |=0r(3|) 73(|-||\|0Mu5|((7|-|47 |-|45 |\|07|-|||\|9 70 |)0 \\/|7|-| 7|-|3 |<3`/93|\| |>r09r4M `/0u \\/r073).
- 0\/3r1`/ "(001" 4|\||) "||\||)u57r|41" 7|-|||\|95 1||<3 |>|-|05|>|-|0r 9r33|\|, (0|\|50135, |\|4|\/ë 4|)M|r47|0|\| 0|= (`/83r-|>u|\||< 4|\||) |-|3r0-(0M|>13><35. 7|-|3 0u7\\/4r|)1`/ 5`/M8015 0|= |-|4(|<3r5. \\/|-|3r3 7|-||5 |)||=|=3r5 |=r0M `/0ur
7\\/3|\|7`/-50M37|-|||\|9, 0r 10|\|9-83|-|01|) 7|-||r7`/-50M37|-|||\|9 |-|4(|<3r/(0|)3r/|7-5|>3(|41|57 |5 |7'5 085355|\/3 |\|47ur3 4|\||) 7|-|3 |)|5(0|\||\|3(7|0|\| 837\\/33|\| 7|-|3 |>r49M47|( 0r|9||\|(39. |>|-|05|>|-|0r 5(r33|\|5: r341|7`/ 0|\| 4|>|>13 ||, (0|\|5013: |=4573r 70 \\/r|73 4 (1| 7|-|4|\| 4 9u|) 0|= 7|-|3 |>|-|3|\|0M3|\|0|\| 4|\||) |7'5 5u|>3r|=|(|41 4|)\/3r7|53M3|\|7 4|\||) 8r|(01493. 5|<r||>7 |<||)|)|35 u53 7|-|3 ||\|57ruM3|\|7 45 4 5747u5 5`/M8015, 1||<3 7|-|3(|\|0\\/ |)37|-|r0\\/|\|3|)) 134|)||\|9 |=u(|<5 0|= 50\/|37 ru55|4 u53|) 7|-|3 |-|4MM3r 4|\||) 5|(|<13.
H0w t0 b3 4 skr1pt k1dd13
- D0wnl04d nm4p, sshnuk3, 4 CS w4llh4ck t00l, B4ck 0rr1f1c3, N3tBus, SubS3v3n, 4nd 4ll s0rts 0f b0tn3t t00ls.
- G4th3r 4nd/0r j01n 4 b0tn3t.
- T4lk 0ut 0f y0ur 4ss.
- H4ck 3v3ry 1P y0u s33.
- DD0S 3v3ry 1P y0u c4n't h4ck.
- Tr0ll 3v3ry0n3 y0u c4n't DD0S.
- H4ck 3v3ry0n3 y0u c4n't tr0ll.
- 3m41l b0mb th3 4dm1ns y0u c4n't h4ck.
- Br4g 4b0ut stuff y0u d1dn't 3v3n d0.
- C4ll 0th3r h4ck3rs scr1pt k1dd13s.
- Tr0ll 3v3ry0n3 wh0 c4lls y0u 4 scr1pt k1dd13.
- Put 4 fl00dn3t 0n #w1k1p3d14.
- Bl4nk p4g3s 0n 3v3ry w1k1 y0u f1nd.
- C4ll 3v3ryth1ng th4t w4lks 4 fuckt4rd.
- D0wnl04d 0th3r h4ck3rs t00ls th3n cl41m th4t y0u wr0t3 th3m.
- G3t b34t3n up by y0ur m4t3s wh0 y0u h4ck3d by 4cc1d3nt.
- G3t b4nn3d fr0m th3 1nt3rn3t.
- Thr34t3n t0 k1ll y0urs3lf 4nd bl4m3 y0ur h4ck3r fr13nds wh3n y0u g3t 4rr3st3d.
- B0n3rs
- ???
- Pr0f1t!!!
Are you a Hacker? by RedDragon
Take a little quiz for me today. Tell me if you fit this description. You got your net account several months ago, possibly even years. You have been surfing the net, and you laugh at those media reports of the information superhighway. You have a red box, and you don't have to pay for phone calls. You have crackerjack, and you have run it on every unix password file you ever come across. Everyone at your school is impressed by your computer knowledge, you are the one the teachers ask for help. Does this sound like you? You are not a hacker.
There are thousands of you out there. You buy 2600 and you ask questions. You read phrack and you ask questions. You join #hack and you ask questions. You ask all of these questions, and you ask what is wrong with that? After all, to be a hacker is to question things, is it not? But, you do not want knowledge. You want answers.
You do not want to learn how things work. You want answers. You do not want to explore. All you want to know is the answers to your damn questions. You are not a hacker.
Hacking is not about answers. Hacking is about the path you take to find the answers. If you want help, don't ask for answers, ask for a pointer to the path you need to take to find out those answers for yourself. Because it is not the people with the answers that are the hackers, it is the people that are traveling along the path.
§ Personality
Don't be an Asshole, Treat people with respect and they will usually do the same. This is especially important at DefCon, you will meet people you've only heard about, don't make that person think you're a total idiot, trust me, they'll talk to you if you're intelligent.
§ Mentality
Hacking is a mentality, you don't decide to do it one day because you saw it on the news, and you want to be kool.
Have you ever gotten something that was brand new and the first thing you want to do is tear it apart to see how it works? I have a friend that goes by "Fraud" that went out and bought himself a brand new cell phone. What's the first thing he did with it when he got home?, that's right, he ripped it apart just to see how it worked.
If you haven't done these things, then why are you here? Why do you want to do this? What motivates you to want to be a Hacker? Do you want to be famous?, or are you in it for the money? Bragging rights? Because there are a lot of people here right now, that really would like to know why. Be honest, we can't make you leave, we just want to know who wants to learn, and who wants to waste our time.
§ CYA
When you watch the documentaries on TV about Hackers, or you see someone who got caught on the news and they start asking them questions, how often is the person they're talking to intelligent, how often do they really know what they're talking about. They may be able to pull the wool over the medias eyes and people over 50 that only know what the media tells them, but do they fool you? Do you recognize that 90% of these people are just kiddies that didn't know their head from their ass when it came to hacking, did something stupid, and got caught. Now we all make mistakes, I'm not saying getting caught makes you a script kiddie, we've all had our brushes with different agencies I'm sure, but all I'm saying is that for the most part, the best hackers know the steps to take to cover their ass, and you better know too.
§ Kiddies
It makes absolutely no sense to be a script kiddie. Now you're not expected to write some program on your own just because you don't want to run someone else's code. That wastes your time, and if it's out there, by all means, use it. That makes about as much sense as writing a new portscanner because you need to scan something and you don't want to use something that's already written because you'll be made fun of. That doesn't mean you shouldn't write new versions of old tools, maybe someone will like yours better than the one they're using now, my point is this, If you're using someone else's code, that's fine, but at least look at the source and know what it does, don't just compile it and go nuts.
Once again, there is nothing wrong with using someone else's code. The difference between a hacker and a script kiddie is that a hacker will look at the code and figure out what it does and either modify it to fit their needs, explore it, or just run it as-is. A script kiddie will simply download and paste whatever shit is given to them.
If you use someone else's code with no understanding of it, you're a script kiddie. Otherwise, you're a hacker.
§ Education
Go and pick up a book, you WILL learn something, most of us (or the companies we work for) pay a ridiculous amount of money to go to schools to teach us these things, and when you get there, they hand you a book, and you read it, you're just paying to sit in a building with a fancy name on the outside.
§ Tools
Know what a port scanner is for, or other tools like them, know what it's used for in the real world and why it was written, know how it works and what you can do with it. I was talking with a friend from 2600 the other day about Etherpeek, when someone asked, what's that? I said it was network monitoring software used by admins to watch what goes on throughout company networks, he summed it up in four words "It's a Packet Sniffer".
§ Ethics
By breaking into an insecure system and justifying it by saying that they should have had better security is insane. We've all heard the analogy, about if you break into someone's house and look around are you not wrong because they should have had better locks? it's the same as when you enter a foreign computer. You have not been given access to this machine, make no illusions about why you should be there, when you enter a machine you haven't been given access to you are breaking the law. I can guarantee your excuses about weak security will not hold up in court.
§ Website Defacement
Website defacement is lame, is running a script, breaking into a site, and defacing their page hacking? No. Does it impress anyone? Maybe your friends that wouldn't know a Linux Box from a Cereal Box, but not us. Try to remember that.
Famous Skript Kiddies
- Kevin Mitnick
- Linus Torvalds
- Anonymous Borg
- Mike Sandy
- Hacking Team
- GNAA
- Spacehero
- MarshviperX
- Xyrix
- 2cash
- Pacifico
- Hacker9
- chatnets
- The entire "Skid Row" script kiddy group.
- LulzSec
- CyberArmy
- AdrenalineOn
- Cutefuzzypuppy
- BlackSquad
- Operation Blueism
| Skript kiddie is part of a series on LERNIN 2 INTERNET 
|
Pitfalls: Aspierations • BLANKING IN PROGRESS • Charming Naïveté • Delete fucking everything • DOIN IT RONG • Edginess • Failing it • Internet tough guy • Kids on the internet • Legal action • Liberalism • Mental illness • Mod Sass • Skript kiddies • Sob Stories • Trolls • Unrealistic Expectations • Unwarranted Self-Importance • Waaaambulance Previous Hiscores: PROTIPS: |
|---|
|
Skript kiddie is part of a series on Security Faggots |
1337 h4x0rz Captain Crunch • Cult of the Dead Cow • David L. Smith • Gary McKinnon • GOBBLES • HD Moore • Jeff Moss • Kevin Mitnick • Lance M. Havok • Robert Morris • Theo de Raadt • weev • Woz
Try-Hards
2cash • AnonOps • Brian Salcedo • Fearnor • Fry Guy • Gadi Evron • g00ns • Hack This Site • Hacking Team • hann • Joanna Rutkowska • John Field • Joseph Camp • Lizard Squad • LulzSec • Mark Zuckerberg • MarshviperX • Masters of Deception • Michael Lynn • Krashed • Raven • r000t • Ryan • Steve Gibson • th3j35t3r • The Regime • Sabu • Zeekill
Related Shit
Avira • Ciscogate • Cloudflare • Conficker • CyberDefender • Defcon • The Gibson • The Great Em/b/assy Security Leak of 2007 • Heartbleed • I GOT NORTON! • Is Your Son a Computer Hacker? • Operation Sundevil • PIFTS.exe • Social engineering • Stylometry • SubSeven • Zone-H |
|---|

|
Skript kiddie is part of a series on Visit the Softwarez Portal for complete coverage. |
