- Portals
- The Current Year
- ED in the News
- Admins
- Help ED Rebuild
- Archive
- ED Bookmarklet
- Donate Bitcoin
Contact an admin on Discord or EDF if you want an account. Also fuck bots.
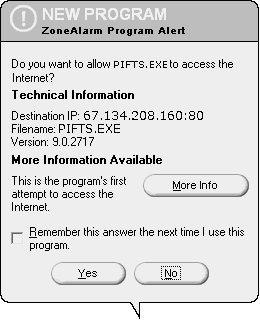
PIFTS.exe



PIFTS.exe is a recent Norton embedded "feature" which is logging all Google searches and cookies, then sending a report to several agencies, including not only Symantec but also Microsoft, a strange server in Africa and a government server in Washington D.C. PIFTS.exe is also known to give your computer AIDS and e-mail your grandmother crude photoshops of your head on top of a gay porno actor being fucked in the ass with a rake.
PIFTS.exe was first discovered by a user on /g/, who was subsequently told to make a thread on the Norton forums to find out just what the fuck was going on. After said post was made, it was deleted by the Norton moderators. It was also soon discovered that all Google references to the Pifts.exe had mysteriously vanished from the interwebs, and that this page is blocked from StumbleUpon.
A PIFT file? In MY temp folder?
Many Norton product users have been discovering a file called Norton_PIFTS 3-9-2009 19h29m27s.txt sitting in their computer's C:\temp folder.

Other PIFTS.exe criminal activity
Below is a list of things that PIFTS.exe is rumored to be responsible for:
- 9/11
- Roswell
- Kennedy's Assassination
- The fall of the Roman empire
- Y2K
- Soulja Boy
- Vanilla Sky
- Armaggeddon 2012
- The LHC
PIFTS: Repercussions of Norton
Use scrollbar to see the full image
Anonymous waited. The firewall notice in front of him blinked and warned out of nowhere. There were trojans in the computer. He didn't see them, but had expected them now for years. His warnings to Norton users were not listened to and now it was too late. Far too late for now, anyway.
Anonymous was safeguarding for 5 years now. When he was young he watched the trojans and said to Norton "I want to help defend against viruses Norton." Norton said "No! You will DOWNLOAD OUR PROGRAM" There was a time when he believed them. Then as he got oldered he stopped. But now in the midst of Anons without UAC or firewalls he knew there would be trojans. "This is /b/" 4chan crackered. "You must fight the pifts!" So Anonymous got his raids and blew up the Norton forums.
"THEY ARE GOING TO KILL US!" said the Norton "I will enable magic_lantern at them" and he started gathering loli and shota information from Anon. Anon explodeded their vans at them and tried to blew Norton up. But then the website fell and they were not able to kill. "No! I must kill the pifts!" Anon shouted
The Digg said, "No, Anon. You are the pifts."
And then /b/ was a pifts.
Magic Lantern: the main target is YOU
Magic Lantern is keystroke logging software developed by the United States' Federal Bureau of Investigation.
Symantec, the makers of Norton AntiVirus and related products, is reportedly working with the FBI on ways to preclude their products from detecting Magic Lantern. Eric Chien, a top researcher at Symantec, emphasized the ability to detect "modified versions."
Also Mcafee are also going down the same route. However Sophos Have said they are not going to leave any backdoors.
In other words, the FBI is watching you masturbate, and they like it.
Norton's Statement
—tl;dr: HAHAHA DISREGARD THAT, I SUCK COCKS. |
This is obviously a damn dirty lie, as the admins were almost instantly deleting all PIFTS.exe-related threads long before /b/, or even /x/ got word of it.
Possible IPs
67.134.208.160:80 & 207.46.248.249:80 Details on IP address 207.46.248.249: OrgName: Microsoft Corp OrgID: MSFT
Address: One Microsoft Way City: Redmond StateProv: WA PostalCode: 98052 Country: US NetRange: 207.46.0.0 - 207.46.255.255 CIDR: 207.46.0.0/16 NetName: MICROSOFT-GLOBAL-NET NetHandle: NET-207-46-0-0-1 Parent: NET-207-0-0-0-0 NetType: Direct Assignment NameServer: NS1.MSFT.NET NameServer: NS5.MSFT.NET NameServer: NS2.MSFT.NET NameServer: NS3.MSFT.NET NameServer: NS4.MSFT.NET 67.134.208.160: IP address: 67.134.208.160 stats.norton.com ISP Qwest Communications Corporation Country: United States
From all this it would seem that Norton, the FBI, Google and Microsoft are all involved. tl;dr: HOLY SHIT WE'RE FUCKED GET YOUR TINFOIL HATS OUT NOW.
The program analyzed
It clearly goes through and scrapes your history, temp files, cookies, etc, and it tries to contact a shady online storage place
they recently acquired. Let's do a lookup on swapdrive! 67.134.208.160:80 is where PIFTS.exe asks to connect to.
Domain Name: SWAPDRIVE.COM
Administrative Contact:
Wallace, Marc
Web Data Group, LC
PO BOX 7241
ARLINGTON, VA 22207-0241
US
703-352-1578
www.webdatagroup.com
Click on " Competitive intelligence." Interesting! They talk about military intelligence gathering right on the page. So this
"update" is scraping internet history and temp data and trying to contact a company who does online storage with shady ties to
intelligence gathering. If it is datamining, Americans need not be surprised, we had AT&T do it on our phones and some act as if
our computers are immune. Hey, let's look more into one of the owners of Swapdrive in the Web Data Group! There are more
interesting people than Marc Wallace.
"Roland Schumann is a former military intelligence officer, having served both on active duty and in the reserves. Trained in
unconventional warfare and electronic intelligence gathering, he also has practical experience in airborne operations, human
intelligence (HUMINT), counter-intelligence, and counter-terrorism. He has performed risk analyses in Latin America for the US
government and in the United States for commercial and government interests."
It is helped to be run by a former military intelligence officer. So there you have it, you have very shady actions by Symantec
regarding the whole thing making people suspicious by deleting any mention of it, they claim it is a simple update, and when we
dive into it, we find out it scrapes your internet history and temp files, interfaces with Google Desktop (G O E C 6 2 ~ 1 . D L L )
, and then where does it try to go? It tries to jump straight to Swapdrive (we know this because it asked permission to
go to 67.134.208.160:80, which is Swapdrive). Who owns swapdrive? The Web Data Group based out of Arlington (wow, the same place the
Pentagon is located, what a coincidence) who has a statement about using military intelligence information gathering right on their
website and who has owners with shady backgrounds as army intelligence officers, and when Symantec is asked about PIFTS.exe, it
immediately tries to cover it up and deletes everything related to it in a very suspicious fashion. Follow the trail, do some research, dig around.
Oh no folks, move along, certainly nothing interesting to see here!
Raid Info

/b/ raided the Norton forums early in the morning on March 10, 2009, following the leak of info about the existence of PIFTS from /g/ to /x/ and eventually to /b/ itself.
Early in the raid, when the wonderful mods still gave a shit, the forums looked something like this. It quickly turned to shit, and lulz ensued all around.
The raid expanded to include trying to Digg the following articles to the front page; Digg (1) and Digg (2).
Most messages were cleaned up and a second shit storm raid has now began.
After loads of EPIC WIN Norton got butthurt and disabled the "New Thread" button.
Gallery
-
It's the fucking Devil
-
BITCHES DON'T KNOW
-
BOUT MY PIFTS.EXE
-
NORTON IS OWNED
-
TIM LOPEZ IS A SPIC LOLOLLOLLL
-
Pifts.exe downloads CP to your PC
-
PIFTS raped my mom and killed my dad
-
PWNED
-
PIFTS has the power to accidentally Africa at will.
-
PIFTS is an anagram for AIDS, didja know that?
-
Just trollin', dawg
-
Norton from symantec message to the internet
-
The "real" story behind PIFTS.
See Also
External Links
- The PIFTS blog
- Reddit (1)
- Reddit (2)
- Norton Forum (POOL'S CLOSED)
- ZOMG CONSPIRACYZ!!111
- Oh lawdy, is dat sum credible news source?
- [1] Their explanation
- The Register: Conspiracy theories fly around Norton forum 'Pifts' purge & Online attackers feed off Norton forum purge
- BUT WHO WAS PIFTS? [2]
|
PIFTS.exe is part of a series on Security Faggots |
1337 h4x0rz Captain Crunch • Cult of the Dead Cow • David L. Smith • Gary McKinnon • GOBBLES • HD Moore • Jeff Moss • Kevin Mitnick • Lance M. Havok • Robert Morris • Theo de Raadt • weev • Woz
Try-Hards
2cash • AnonOps • Brian Salcedo • Fearnor • Fry Guy • Gadi Evron • g00ns • Hack This Site • Hacking Team • hann • Joanna Rutkowska • John Field • Joseph Camp • Lizard Squad • LulzSec • Mark Zuckerberg • MarshviperX • Masters of Deception • Michael Lynn • Krashed • Raven • r000t • Ryan • Steve Gibson • th3j35t3r • The Regime • Sabu • Zeekill
Related Shit
Avira • Ciscogate • Cloudflare • Conficker • CyberDefender • Defcon • The Gibson • The Great Em/b/assy Security Leak of 2007 • Heartbleed • I GOT NORTON! • Is Your Son a Computer Hacker? • Operation Sundevil • PIFTS.exe • Social engineering • Stylometry • SubSeven • Zone-H |
|---|

|
PIFTS.exe is part of a series on Visit the Softwarez Portal for complete coverage. |
| Featured article March 12, 2009 | ||
| Preceded by Is This Battletoads |
PIFTS.exe | Succeeded by Louise Ogborn |